An extremely advanced Bitcoin-based ransomware trojan was discovered by security experts last month. It’s the first malware of this kind to use TOR network to anonymously communicate with a central command and control server.
Ransomware is a kind of malware that tends to block access to certain systems of the computer that it infects. It demands the user of the computer to pay a ransom to the operator of the scam in order for the restrictions to go away. Many ransomware trojans try to trick users into paying a “fine” by claiming to be software directed by the law authorities, falsely accusing people for child pornography possession or downloading pirated content.
Other badware of the ransomware family search computers for files stored by the users, like photos or documents, then uses cryptography to encrypt them so they can no longer be accessed by the person using the infected machine. Τhis is a similar tactic to the one Cryptolocker, a ransomware trojan that reached it’s peak last year was using. Cryptolocker’s operators managed to collect millions of dollars worth of Bitcoin before the FBI managed to shut down the criminal operation by busting the command-and-control servers Cryptolocker was using Back in May 2014.
Bitcoin-demanding “Critroni” is the most advanced ransomware experts have seen to date
In the last decade the ransomware criminal industry has seen some massive growth. From simple screen blockers that require a payment to go away, to badware using advanced technologies to force people into paying their ransom. Ransomware is now reaching it’s peak, with new age trojans using what is called encryptors. Programs that would encrypt user files and demand a payment for the file blockage to go away and the files to get decrypted. Some examples of such trojans are CryptoLocker, CryptoDefence, CryptoWall, ACCDFISA, and GpCode but also many other lesser known similar fundamental software that had spread around Russia. The newly discovered trojan, Critroni, was brought to life mid June 2014. It has since been advertised in various underground forums. It’s being described as the new generation of Bitcoin ransomware, and is not similar to any of it’s ancestors. It’s known that the new malware called is using techniques never used before by any other malware.
One of it’s unique features is that Critroni uses the anonymous TOR network to communicate with it’s command servers anonymously. Computers infected by it are in fact communicating with the central command server of the ransomware through TOR. This way makes it able to send a key stored in the server after the Bitcoin ransom is paid, and this key is the only chance users of the infected machines will get to decrypt their files.
Critroni (also known as CTB-Locker) might not be the first malware to use TOR to hide it’s roots, but this certainly is the first time that we see ransomware to do it. However, that is not the biggest advantage Critroni has. Critroni is also the first malware to use TOR code embedded directly in it’s own files rather than relying on the legitimate TOR bundle software to accomplish communications.
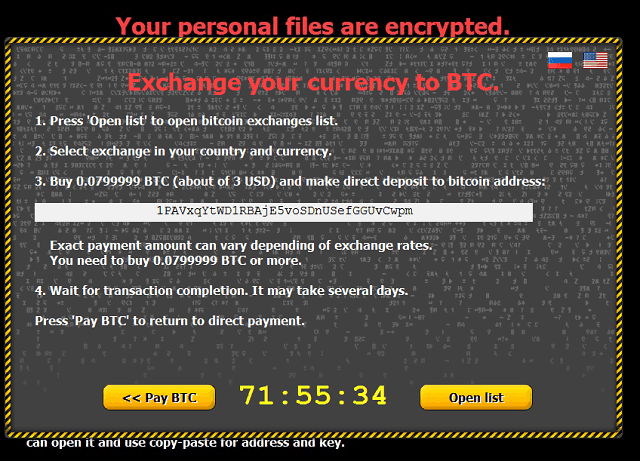
Critroni is also using one of the most bizarre, yet effective, encryption schemes ransomware has even used to block user access to files. Data is first compressed using the encryption algorithm ECDH (Elliptic Curve Diffie-Hellman). In contrast to the most commonly used combination of algorithms amongst ransomware AES and RSA, ECDH will not allow user data to be decrypted even if the connection between the communication of the virus with the command server is stopped. This way practically making paying the (usually up to) 0.4 Bitcoin ransom the only way for the user to restore the encrypted files.
How this Bitcoin ransomware spreads
In it’s early versions critroni would mainly target English speaking users. Therefore English was the only language in the program. In some later versions, Russian also started to be supported next to the English language. The new updates also brought a countdown timer to the GUI. This way giving users a time warning in an attempt to intimidate them.
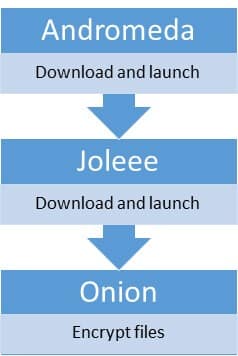
The image below roughly depicts how the malicious software installs and propagates itself. First, the Andromeda bot downloads and runs a tool named Joleee. This malicious tool can send out spam emails as well as to execute commands received from the cybercriminals. It’s Jolee that dowloads the encryptor to the infected computer.
Bitcoin payments and TOR
It is not hard to notice that the creators of the virus are putting a lot of effort into staying anonymous. They have good reason to, and it’s not just because what they’re doing is considered criminal activity. By making their software use an anonymous network, they’re also contributing to their ransomware having a more longterm lifespan. As mentioned before, back in May the FBI managed to shut down another encryptor ransomware called Cryptolocker. They managed to track their servers and shut them down. This could be much harder with Critroni’s case since it’s receiving commands through TOR. This combination of TOR embedding, and Bitcoin payments, has allowed it to top the anonymity of it’s predecessors.
Recommendations on how to stay safe, and keep your Bitcoin
Having security software such as an antivirus enabled and updated can be vital. However that’s not an end of the line solution.
The best way to ensure your files will be safe is to make your own backups, and ransomware is not the only reason you should do that. You should never store a file that is important to you only in one place. It’s more likely that important personal files are not taking a big part of your hard drive. Making an offline backup, to an external drive or usb stick, isn’t hard and is a reliable way of making secure backups. What you should keep in mind when making backups though, is that the storage device should not be directly connected to the internet. Whether it’s a USB, an external hard drive or a floppy disc, having it constantly connected to your personal computer with internet access will make it as vulnerable to encryption ransomware as your main hard drive storage. Online storage is fine too, but no one can guarantee it’s long term existence.
Beyond that, while this ransomware is encrypting files in a malicious way, it is always a good idea to personally encrypt any sensitive, or valuable, files, such as a Bitcoin wallet. This will make it much more difficult for malware, or hackers, to successfully steal your files in a way that would be usable.

 4 Comments
4 Comments

what is that?
Thank you So much
nice post
thank you very much for the info.