In the past year Bitcoin started to act as the preferred form of currency to a new type of malicious software. It’s called Ransomware in general and it takes your computer files as hostage until you pay the hacker who created it his ransom.
And it’s evolving, fast…
The first and most notorious form of ransomware requesting Bitcoin was called “CryptoLocker”. It sneaks up to your computer through innocent looking SPAM emails like this one.
Attached to the email was a ZIP archive containing a small executable file (a program that runs on a Windows computer, usually ends with “.exe”). To make things even harder to detect the “.exe” file was using a document extension (i.e. “.pdf”) in the filename and displaying an Adobe Reader icon.
If you chose to open the malicious file, it would download and execute Gameover ZeuS, which in turn downloads and installs other malware families including CryptoLocker. CryptoLocker will then go ahead and encrypt your computer files so you won’t have access to them without a specific private key (just like the one used in a Bitcoin wallet). Of course in order to get the private key, you’ll need to pay.
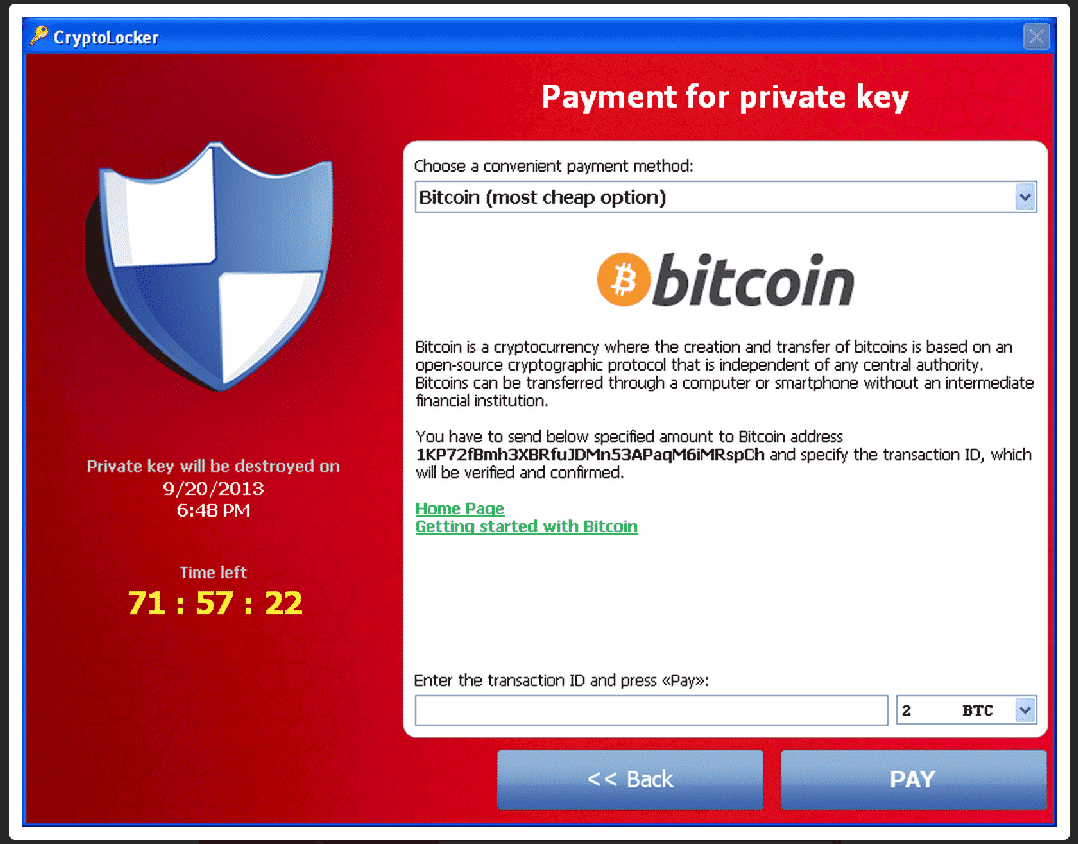
This is what you’ll see on your computer if you’re infected:
If you didn’t manage to pay the ransom in time you would need to use CryptoLocker’s “decryption service”. Of course, CryptoLocker’s “Decryption Service” is much more expensive than the original ransom.
This is crazy:
In the first 100 days CryptoLocker was released almost 500,000 computers got infected. According to Symantec 3% of people agree to pay ransom but additional studies suggest that the number is closer to 1.3%.
One Thesis claims that the creators of CryptoLocker were able to collect 1,216 BTC throughout this time period, making them a profit of several hundred thousand dollars.
CryptoLocker was finally shut down on June 2nd 2014 when several law enforcement agencies took down the network that operates it. Users who were infected were now able to decrypt back their files using a website called DecryptCryptoLocker.
But the story didn’t end there:
Inspired by CryptoLocker, although not related, CryptoWall came to play around February 2014. Even though CryptoWall was less sophisticated than CryptoLocker it managed to infect 625,000 computers – a larger number than its predecessor.
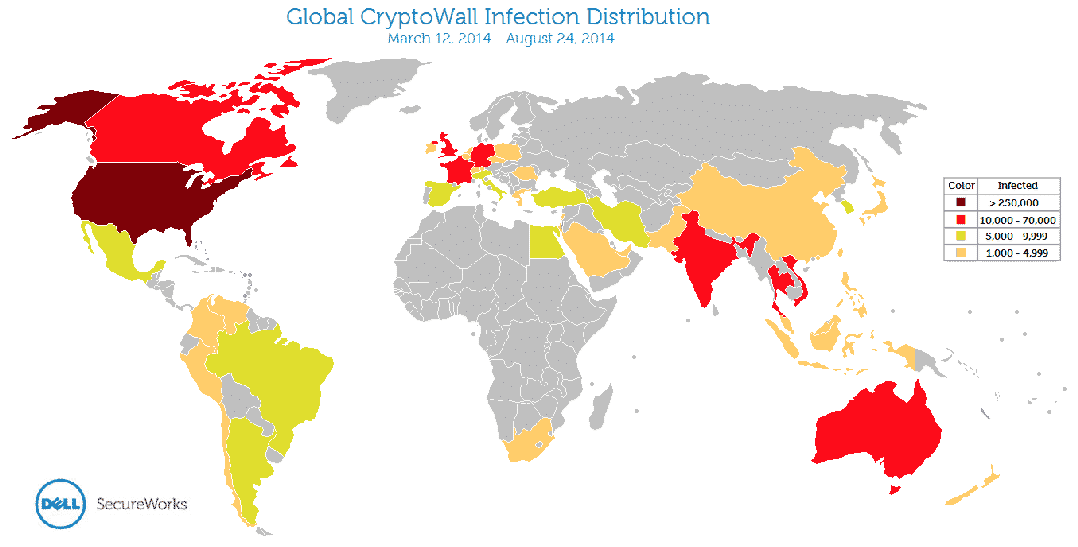
Top infected countries were the US, Vietnam, UK and Canada. Here’s a geographical representation of the infected countries:
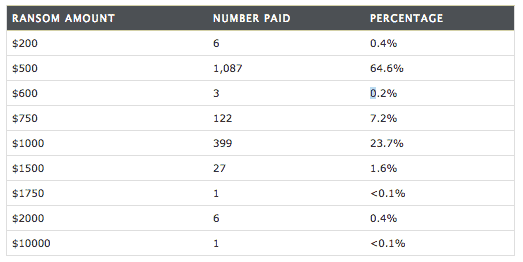
But even though a lot of effort was made to distribute CryptoWall as much as possible the results were a bit disappointing. “Only” 939 BTC were collected from different uses who decided to pay. The ransom varied between $200 and $10,000 (which was paid by only one user).
The bad news is that CryptoWall is evolving:
While CryptoWall started out as a CrptoLocker clone, it now has mutated into an CryptoWall 2.0 on January 2015 and to CryptoWall 3.0 on March 2015. Today CryptoWall not only encrypts your files but can also steal information from your computer, including your Bitcoin wallet’s private key. This makes the software much more profitable to its creators by ensuring they will get some form of payment for their work.
In the past few months of 2015 these two major threats have also been reported:
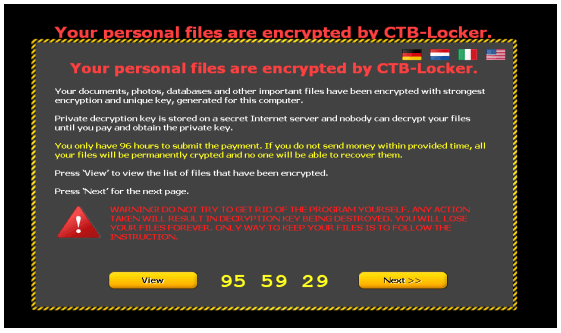
CTB Locker – Stands for Curve-Tor-Bitcoin.
- Curve comes from cryptography which is based on elliptic curves. This is the method used to encrypt your files.
- Tor (stands for The Onion Router) is a network of computer which comprise the Darknet.
- Bitcoin refers to the possibility to pay in bitcoins.
Here’s how a “hijacked” computer with CTB Locker looks like:
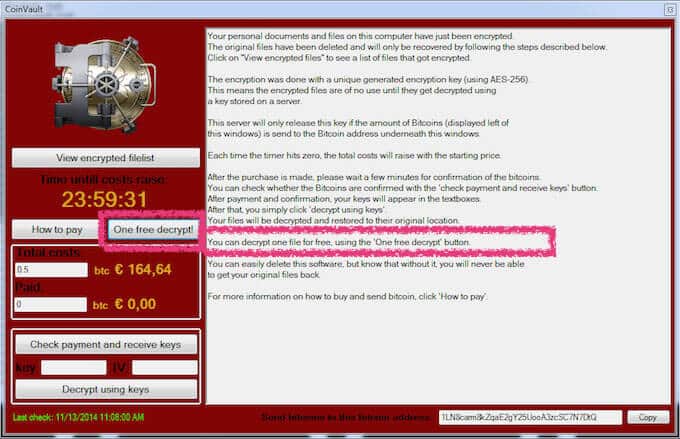
CoinVault – Released on November 2014, this CrpytoGraphic Locker gives you the option to decrypt one file “on the house”. Meaning, the creators of the software want to give you a taste, or some sort of proof, that they are good for their word. Consider it an act of good faith, like setting one hostage free.
CoinVault has targeted over 20 countries to date, but the Netherland police were able to achieve some of CoinVault’s information. Using this info Kaspersky has set up a decryptor website to help fight CoinVault.
But there are good news as well:
There’s something you can do about this increasing phenomenon of CryptoGraphic Lockers .
First of all, the types of ransomeware I’ve mentioned in this post all target different Microsoft Windows versions (from XP up to Windows 10). So if you have a mac and you are using the Mac OS you’re probably safe (probably…).
Second, you should make it a habit to regularly back up your files. This way, even if someone encrypts your data you can always restore the original files without the encryption. Since connected services like Dropbox may also be infected depending on the case, an offline backup is also suggested.
If you’re going to back up your files you may want to follow the 3-2-1 rule which means:
- 3 different copies on three different places (3 copies on the same hard-drive doesn’t count).
- 2 different formats (e.g. hard-drive and DVD).
- Keep 1 copy off-site (i.e. in a different location). This will prevent both copies getting destroyed in case of a break-in, fire, etc.
The next measure to take is pretty simple. Don’t open email attachments that look funny (ok mom?!). This includes emails from people you don’t know and files that you think may be unsafe. It’s been noted that even files that may seem harmless like Powerpoint presentations,Excel sheets and Word documents. can also include an executable file within them.
Make sure to always update your operating system with the latest updates and have a reliable Anti-Virus program installed. Following these steps will probably have you covered in most cases. If you feel you want additional protection you can refer to this guide which supplies advanced steps that can be taken.
Apparently there are also dedicated tools you can install on your computer to prevent these types of ransomeware from showing up like CryptoPrevent and CryptoGuard.
Last but not least, there is a huge resource regarding CoinVault in particular which will give you all of the information you need in case you get infected here.
If you’ve ever had your computer infected with ransomeware I’d love to hear your story in the comment section below.
Sources:

 11 Comments
11 Comments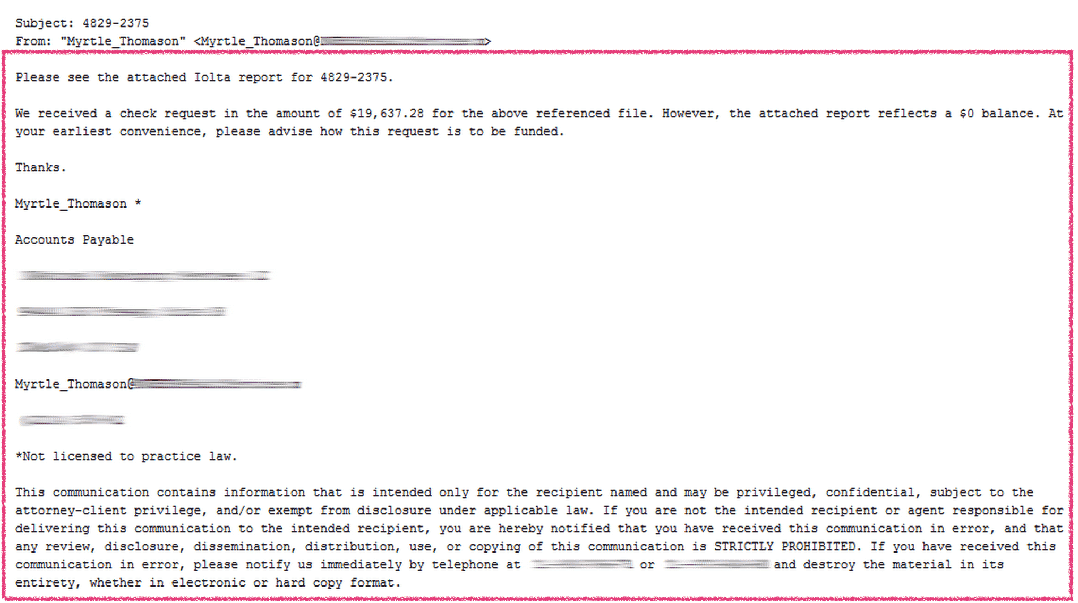


Thank you for letting us know 😉
You’re welcome
Great post! Thanks for informing us on these new types of malware! It’s important we know about them and how to avoid them.
Can’t believe so many people got infected and some actually paid! These people must not know about these kinds of threats, otherwise why would they open or download suspicious stuff? With more knowledge like this article, everyone would know what to do and what not to do and such malware would become irrelevant.
I wonder who is really behind these ransomware. Could it be an antivirus company? Someone rich who wants more money? It’s sad to see people trying to get money this way. Just do something meaningful with your life not try to extort others.
There are many suspicions against the Antivirus companies regarding whether or not they create these viruses. You can see an interesting thread here: http://www.quora.com/How-do-antivirus-companies-find-new-viruses
I never open any emails from people I don’t know and even if I get emails from people I do know I always think twice before clicking any links or downloading anything. I usually just don’t download anything.
I got infected with this ransomware some time ago but thankfully I used DecryptCryptoLocker and got all my files back :)! I was scared at first when this happened but I kept my calm and tried to find solutions. I never even considered paying.
Hi
I currently have this ransomware issue, and I was wondering with your case, have all your files been added a .ttt extension at the back of your files?
Do you know if DecryptCryptoLock would help in my case, as I really would like to get all the files especially those pictures of my son back.
Appreciate and look forward to your feedback soon. Thanks!